Updates to Dell Endpoint Security Suite Enterprise Advanced Threat Protection detection method
摘要: Updates to Dell Endpoint Security Suite Enterprise or Dell Threat Defense may cause changes in how threats are evaluated.
症状
- As of May 2022, Dell Endpoint Security Suite Enterprise has reached End of Maintenance. This article is no longer updated by Dell. For more information, reference the Product Life Cycle (End of Support / End of Life) Policy for Dell Data Security. If you have any questions on alternative articles, either reach out to your sales team or contact endpointsecurity@dell.com.
- As of May 2022, Dell Threat Defense has reached End of Maintenance. This article is no longer updated by Dell. For more information, reference the Product Life Cycle (End of Support / End of Life) Policy for Dell Data Security. If you have any questions on alternative articles, either reach out to your sales team or contact endpointsecurity@dell.com.
- Reference Endpoint Security for additional information about current products.
Affected Products:
- Dell Endpoint Security Suite Enterprise
- Dell Threat Defense
Affected Versions:
- 1.2.137x
- 1.2.139x
- 2.0.145x
原因
Dell Data Protection's Advanced Threat Protection products; Dell Threat Defense, and Dell Endpoint Security Suite Enterprise may have occasional updates that change how threats are evaluated. These updates are commonly referenced as "model" updates, as they are updates to the threat model.
解决方案
To help users know how a new model might affect their organization, there are two columns on the Protection page in the Console. You can use the Production Status and New Status comparison to see which files on your devices that the model change as impacted.
Users should test the new models before a full production roll-out. This should minimize any unintended outages cause by model changes.
The scenarios that you should be aware of are:
- A file that was considered Safe in the Current Model might change to Unsafe in the New Model. If your organization needs that file, you can add it to the Safelist.
- A file that the Current Model has never seen or scored, and the New Model considers it Unsafe. If your organization needs that file, you can add it to the Safelist.
New Protection Columns
The two columns are: Production Status and New Status:
- Production Status: Displays the current model status (Safe, Abnormal, or Unsafe) for the file
- New Status: Displays the model status for the file in the new model
Only files found on devices in your organization that have changes in their Threat Score are displayed. Some files might have a Threat Score change but remain within their current Status.
Examples:
The Threat Score for a file goes from 10 to 20, the file status would remain Abnormal, and the file appears in the updated model list (if this file exists on devices in your organization).
To view the Current Model and New Model columns:
- Log in to the Dell Data Protection Remote Management Console, select Populations -> Enterprise -> Advanced Threats, then select the Protection tab.
- Click the down arrow on a column header.
- Select the Production Status and New Status columns.
- Click the down-arrow or click anywhere on the page to close the column options menu.
You can now review the differences between the two Threat Models.
The two scenarios you should be aware of are:
- Current Model = Safe, New Model = Abnormal, or Unsafe
- Your Organization considers the file as Safe or the Classification is Trusted Local.
- Your Organization has Abnormal or Unsafe set to Auto Quarantine (AQT).
- Current Model = Null (not seen or scored), New Model = Abnormal or Unsafe
- Your Organization considers the file as Safe or the Classification is Trusted Local.
- Your Organization has Abnormal or Unsafe set to Auto Quarantine (AQT).
In the above scenarios, the recommendation is to Safelist the files you want to allow in your organization.
Identify Classifications
To identify classifications that could impact your organization, we recommend the following approach:
- Apply a filter to the New Model column to display all Unsafe, Abnormal, and Quarantined files. If your policy is set to Auto-Quarantine, you cannot see any Unsafe or Abnormal files because these threats have been quarantined.
- Apply a filter to the Production Status column to display all Safe files.
- Apply a filter to the Classification column to only show Trusted - Local threats. Trusted - Local files are analyzed with Dell's ATP and found to be safe (safelist these items after review). If you have a lot of files in the filtered list, you may want to prioritize using more attributes. Example: Add a filter to the Background Detection column to review threats found by Execution Control. These were convicted when a user attempted to run an application and need more urgent attention than dormant files convicted by Background Threat Detection or File Watcher.
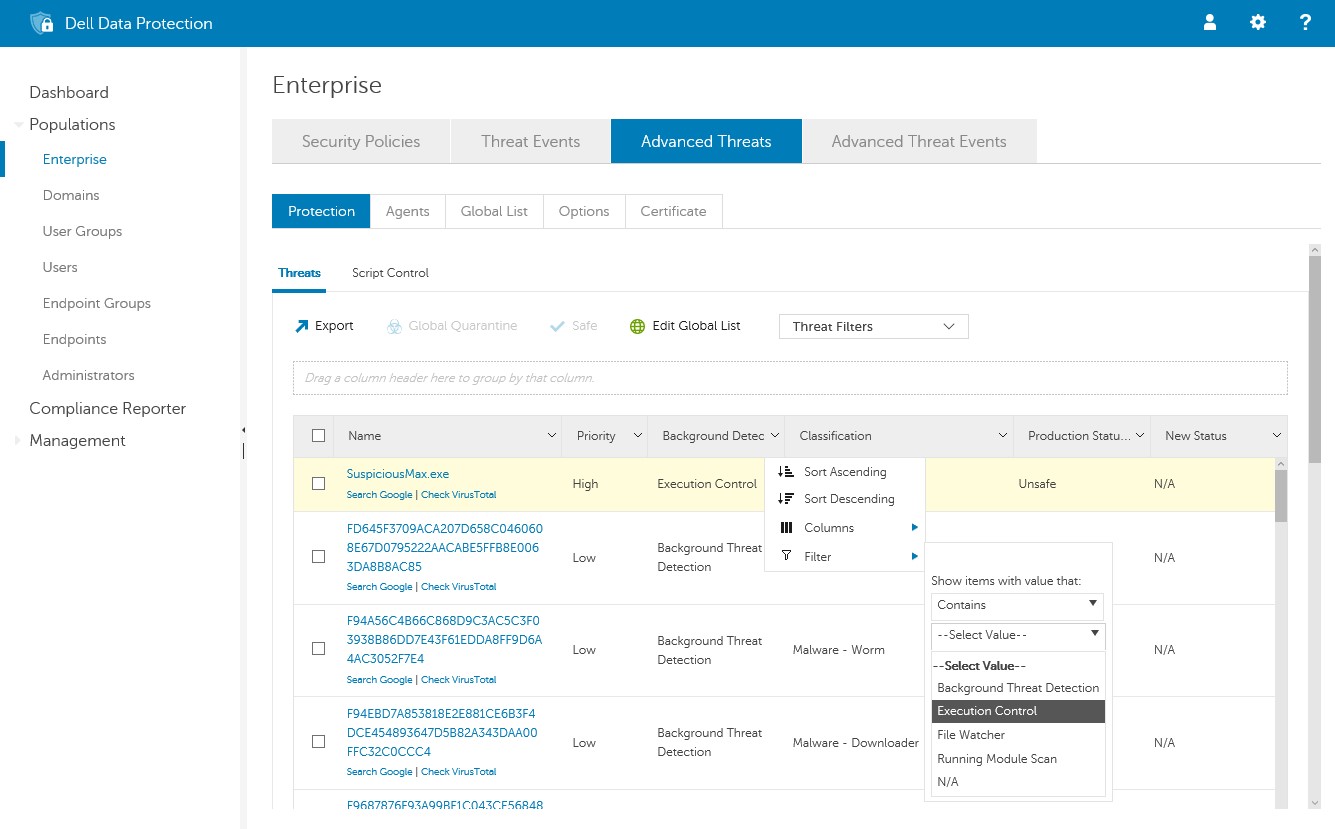
Figure 1: (English Only) Advanced Threats
Recommended Production Roll-out
This section outlines strategies to help users upgrade to a newer predictive model. It is highly recommended to assign Agents to a Policy with Auto-Quarantine that are enabled for Unsafe and Abnormal files.
Auto-Updates with Auto-Quarantine
If Agents are set to Auto-Update, you should disable auto-updates for agents when new predictive models are released. If it is not possible to disable Auto-Quarantine or test the new Agent, alert your Dell Data Protection Administrators. They may want to Safelist items that are misclassified to unblock users.
Manual Updates with Auto-Quarantine
If you manually update Agents, then Auto-Update is not a concern. It is recommended that you use the following instructions before updating your Agents.
- Test the new Agent (with the new model) on a representative set of computers. Ideally, these test machines would be placed in an Auto-Quarantine policy. If a Safe application is getting blocked, add the file to your Safelist.
- Once testing is complete, roll out the new Agent to all your computers.
To contact support, reference Dell Data Security International Support Phone Numbers.
Go to TechDirect to generate a technical support request online.
For additional insights and resources, join the Dell Security Community Forum.