How to Identify a File's SHA-256 Hash for Security Applications
Sommaire: Learn about how to identify a file’s SHA-256 hash by following these instructions. Hashes can be used to exclude a file in security applications.
Cet article s’applique à
Cet article ne s’applique pas à
Cet article n’est lié à aucun produit spécifique.
Toutes les versions de produits ne sont pas identifiées dans cet article.
Symptômes
A secure hash algorithm (SHA)-256 hash may be required to exclude a file from an anti-virus or malware prevention application. This article discusses how to identify the SHA-256 hash for a file on Windows, macOS, or Linux.
Affected Operating Systems:
- Windows
- macOS
- Linux
Cause
Not applicable
Résolution
Click Windows, macOS, or Linux for the process to identify the file's SHA-256 hash.
Windows
- Right-click the Windows Start menu and then click Run.
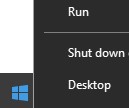
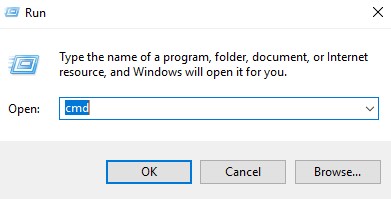
- In the Run UI, type
cmdand then press OK.
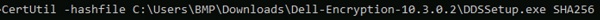
- In Command Prompt, browse to the location of the appropriate [FILENAME].
Note: [FILENAME] = Name of file.
- Type
CertUtil -hashfile [FILENAME] SHA256and then press Enter.
Note:
[FILENAME] used in the example may differ in your environment.
- Record the file’s SHA-256 hash. In the example,
5e71d4ffc3a0723b1bcca206fd14c0e217f6d9beb33a5b327ea251d3a54df5afis the file’s SHA-256.
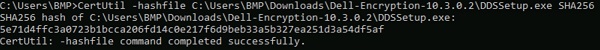
Note: The SHA-256 hash in the example may differ in your environment.
macOS
- Select Go, then Utilities, and then Terminal.
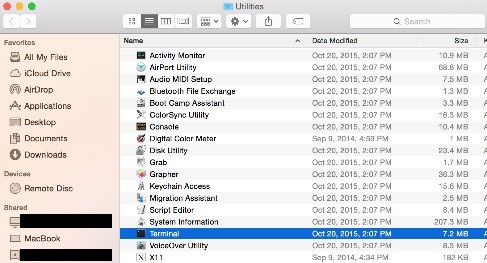
- Double-click Terminal to launch the UI.
- In terminal, browse to the location of the appropriate [FILENAME].
Note: [FILENAME] = Name of file.
- In Terminal, type
sudo shasum -a 256 [FILENAME]and then press Enter. - Populate the Password for the account being used and then press Enter.

Note: [FILENAME] used in the example may differ in your environment.
- Record the file’s SHA-256 hash. In the example,
56429c53bff44bbf21527f0bf13a27bc20ceff42160d3170287af6d50da195623is the file’s SHA-256.
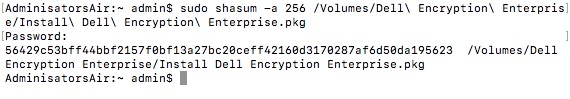
Note: The SHA-256 hash in the example may differ in your environment.
Linux
- Open Terminal.
- In Terminal, browse to the appropriate [FILENAME].
Note: [FILENAME] = Name of file.
- Type
sudo sha256sum [FILENAME]and then press Enter. - Populate the password for the account being used and then press Enter.
- Record the file’s SHA-256 hash. In the example,
4167b599f36af0781b81563bd2179a6d35daa3145f0b6f99ac6d9ee1894b516ais the file’s SHA-256.
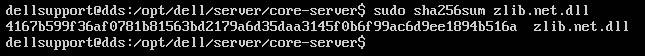
Note: The [FILENAME] and SHA-256 hash in the example may differ in your environment.
To contact support, reference Dell Data Security International Support Phone Numbers.
Go to TechDirect to generate a technical support request online.
For additional insights and resources, join the Dell Security Community Forum.
Produits touchés
Dell EncryptionPropriétés de l’article
Numéro d’article: 000130826
Type d’article: Solution
Dernière modification: 13 nov. 2023
Version: 8
Obtenez des réponses à vos questions auprès d’autre utilisateurs de Dell
Services de soutien
Vérifiez si votre appareil est couvert par les services de soutien.