How to Allow Dell Data Security Kernel Extensions on macOS
Zusammenfassung: Learn how to allow kernel extensions for Dell Endpoint Security Suite Enterprise for Mac, Dell Threat Defense, Dell Encryption Enterprise for Mac, CrowdStrike Falcon Sensor, or VMware Carbon Black Cloud Endpoint. ...
Weisungen
- As of February 2021, Dell Encryption Enterprise for Mac has reached End of Maintenance. This product and its articles are no longer updated by Dell.
- As of May 2022, Dell Endpoint Security Suite Enterprise has reached End of Maintenance. This product and its articles are no longer updated by Dell.
- As of May 2022, Dell Threat Defense has reached End of Maintenance. This product and its articles are no longer updated by Dell.
- For more information, reference Product Life Cycle (End of Support and End of Life) Policy for Dell Data Security. If you have any questions on alternative articles, either reach out to your sales team or contact endpointsecurity@dell.com.
- Reference Endpoint Security for additional information about current products.
System Integrity Protection (SIP) was hardened in macOS High Sierra (10.13) to require users to approve new third-party kernel extensions (KEXTs). This article explains how to allow Dell Data Security kernel extensions for the macOS High Sierra and later.
Affected Products:
- Dell Endpoint Security Suite Enterprise for Mac
- Dell Threat Defense
- Dell Encryption Enterprise for Mac
- CrowdStrike Falcon Sensor
- VMware Carbon Black Cloud Endpoint
Affected Operating Systems:
- macOS High Sierra (10.13) and Later
Users encounter this security feature if:
- Performing a new install of:
- Dell Threat Defense
- Dell Endpoint Security Suite Enterprise
- Dell Encryption Enterprise for Mac
- CrowdStrike Falcon Sensor
- VMware Carbon Black Cloud Endpoint
- SIP is enabled.
Users do not encounter this security feature if:
- Performing an upgrade of:
- Dell Threat Defense
- Dell Endpoint Security Suite Enterprise
- Dell Encryption Enterprise for Mac
- CrowdStrike Falcon Sensor
- VMware Carbon Black Cloud Endpoint
- SIP is disabled.
Allowing kernel extensions differs between User Experience and Enterprise Deployments. Select the appropriate option for more information.
User Experience
If SIP is enabled on macOS High Sierra or later, the operating system experiences an extension block alert post install of Dell Endpoint Security Suite Enterprise, Dell Threat Defense, Dell Encryption Enterprise for Mac, CrowdStrike Falcon Sensor, or VMware Carbon Black Cloud Endpoint. This may read as, "System Extension Blocked - A program tried to load new system extension(s) signed by "[NAME]". If you want to enable these extensions, go to the Security & Privacy System Preferences pane."
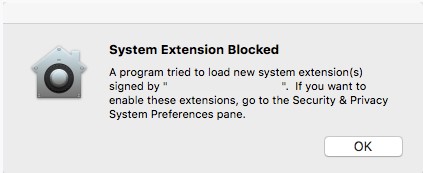
- Dell Inc, formerly Credant Technologies
- Credant Technologies
- Benjamin Fleischer (if Encryption External Media policy is enabled)
Approving the extension differs depending on the version of macOS installed. For more information, click either v11.X (Big Sur) or v10.13.X to 10.15.X (High Sierra, Mojave, and Catalina).
v11.X (Big Sur)
With the advent of system extensions in macOS Big Sur, there are instances when Kernel Extensions may not be properly loaded on new installations of applications. Applications that were installed before the upgrade to macOS Big Sur should have the kernel extensions pre-imported.
If applications are failing to properly start, the TeamID for the application may be manually entered outside of the operating system.
- Start up the affected Mac in recovery mode.
Note: For more information, reference About macOS Recovery on Intel-based Mac Computers: https://support.apple.com/102518
.
- Click the Utilities menu and then select Terminal.
- In Terminal, type
/usr/sbin/spctl kext-consent add [TEAMID]and then press Enter.Note:[TEAMID]= The Apple TeamID for the product being installed- Apple TeamIDs:
- Dell Endpoint Security Suite Enterprise:
6ENJ69K633 - Dell Threat Defense:
6ENJ69K633 - Dell Encryption Enterprise:
VR2659AZ37- Dell Encryption External Media:
3T5GSNBU6W(v10.1.0 and earlier) - Dell Encryption External Media:
VR2659AZ37(v10.5.0 and later)
- Dell Encryption External Media:
- CrowdStrike Falcon Sensor:
X9E956P446 - VMware Carbon Black Cloud Endpoint:
7AGZNQ2S2T
- Dell Endpoint Security Suite Enterprise:
- For example, if VMware Carbon Black Cloud Endpoint must be manually added, type
/usr/sbin/spctl kext-consent add 7AGZNQ2S2Tand then press Enter.
- Close the Terminal app and restart into macOS.
v10.13.X to 10.15.X (High Sierra, Mojave, and Catalina)
- Log in to the affected Mac.
- In the Apple Dock, click System Preferences.

- Double-click Security & Privacy.

- Under the General tab, click Allow to load the KEXT.
 Note: The Allow button is only available for 30 minutes post installation. Until the user approves the KEXT, future load attempts cause the approval UI to reappear, but do not cause another user alert.
Note: The Allow button is only available for 30 minutes post installation. Until the user approves the KEXT, future load attempts cause the approval UI to reappear, but do not cause another user alert.
Enterprise Deployments
An Apple management solution (such as Workspace One, Jamf) can use an Apple TeamID to suppress user approval of a KEXT.
- Apple TeamIDs:
- Dell Endpoint Security Suite Enterprise:
6ENJ69K633 - Dell Threat Defense:
6ENJ69K633 - Dell Encryption Enterprise:
VR2659AZ37- Dell Encryption External Media:
3T5GSNBU6W(v10.1.0 and earlier) - Dell Encryption External Media:
VR2659AZ37(v10.5.0 and later)
- Dell Encryption External Media:
- CrowdStrike Falcon Sensor:
X9E956P446 - VMware Carbon Black Cloud Endpoint:
7AGZNQ2S2T
- Dell Endpoint Security Suite Enterprise:
To verify an endpoint’s allowlisted Apple TeamIDs:
- On the endpoint, open Terminal.
- Type
sudo kextstat | grep -v com.appleand then press Enter. - Populate the superuser Password and then press Enter.
To contact support, reference Dell Data Security International Support Phone Numbers.
Go to TechDirect to generate a technical support request online.
For additional insights and resources, join the Dell Security Community Forum.