Along with the Department of Homeland Security and others, we at RSA sponsor National Cyber Security Awareness month in October. But, we need more than just awareness. We need context, not a litany of the latest breaches, but an understanding – a better, broader, more collaborative understanding of the problems IT organizations are facing and the enemies we are fighting.
Is it possible that the problem is overhyped? Yes and No. This is a complex issue that the press has a hard time reporting. And perhaps, just perhaps, they occasionally over-sensationalize what happens. But no, it’s not overhyped. The press unfortunately doesn’t see what we, law enforcement, and defense organizations see. Nobody wants their breach or loss exposed. So, like an iceberg, the true depth of the problem remains hidden. The result is a serious gap between the perception and the reality of the problem.
According to Verizon Research Reports, most organizations don’t even know they’ve been breached. And the lack of a comprehensive system to share information in timely manner only exacerbates the problem.
The implication is that security models are not moving fast enough to make the transition from traditional perimeter-based security to new intelligence-based security, while adversaries become more sophisticated.
In the last year, in my conversations with CIOs, Boards of Directors and customers, I get agreement that a new model of cyber-security is needed. What is it? An intelligence-based security system consisting of multiple components. The first is qualitative – a thorough understanding of risk – with risk mitigation strategies that, when implemented, produce compliance as a by-product. The next two are technology-oriented – the use of agile controls based on pattern recognition and predictive analytics, and the use of big data analytics to give context to vast streams of data from numerous sources to produce timely, actionable information. These types of controls and analytic engines are dynamic and synergistic giving you true defense in depth. Of course there is a requirement for personnel with the right skill set to operate the system. And the final component that intelligence-based security requires is information sharing at scale.
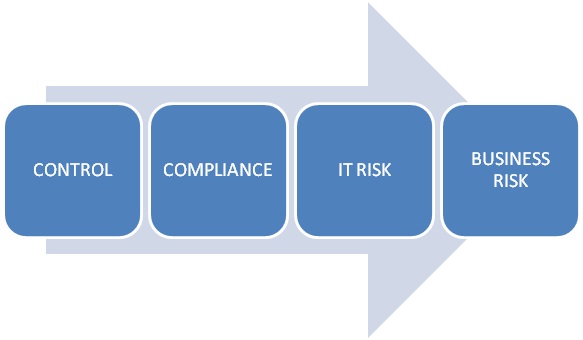
Confusion about what to do abounds because of this perception gap as well as an increasing gap between sophisticated and naive IT organizations, largely based on the aptitude of personnel. The scariest part of this is that size doesn’t matter. Let me illustrate a spectrum of cyber-security maturity. These four blocks represent the primary attributes of the least mature to the most mature – going from left to right.
Cyber-Security Maturity Spectrum
Those in the Control category are stuck in the most elementary approach that doesn’t see or go far enough. They just want the problem to go away. Give me a box or a piece of software and as the commercial says, let me set it and forget it. These are the uninformed ones. If they are not totally compromised, they are lucky. They are just a botnet node in the making.
The Compliance category is about organizations that just want to tick a box to say they have complied with policy. They are heavily regulated or so monomaniacally focused on ISO 27001 that they are more concerned with the form over the substance of what they’re doing. What they don’t seem to understand is that a good governance model, a thorough understanding of risk and related mitigation capabilities, will create compliance as a bi-product of doing the right thing in the first place. In fairness to them, they are usually under extreme pressure from those above or from regulators.
The IT Risk category is about organizations that understand the threat and are taking the right steps to evolve their security infrastructures. They are only slightly behind the Business Risk category – which is the highest level of maturity. These organizations see opportunities to change their business models based on all the technology available to them, taking maximum advantage of mobility and the cloud, and they’re moving their security infrastructures in concert with these changes. Where the IT Risk category is tactical, the Business Risk category is the most focused and strategic. That’s what we should all aspire to.
The less mature categories are not just small and medium size organizations. Some of these organizations are quite large and I see them all the time. They are part of critical infrastructures or they have valuable IP that is critical to a nation’s economy and health. It’s a cliché, but we are only as strong as our weakest link and we are interdependent as never before. Attacks on one of us have the potential to be attacks on us all.