 US$1,000,000,000. That’s the estimated cost of ransomware to individuals and businesses in 2016. In the first quarter of 2016 alone, ransomware cost organizations US$209 million. Keep in mind that ransomware is just one type of cybercriminal activity. Although final numbers for 2016 are not yet known, based on the frequency and sophistication of the attacks so far, it’s likely that 2016 will end up as the most lucrative year on record for cybercriminals. The latest numbers show that there were more than 2 billion records leaked in 2016.
US$1,000,000,000. That’s the estimated cost of ransomware to individuals and businesses in 2016. In the first quarter of 2016 alone, ransomware cost organizations US$209 million. Keep in mind that ransomware is just one type of cybercriminal activity. Although final numbers for 2016 are not yet known, based on the frequency and sophistication of the attacks so far, it’s likely that 2016 will end up as the most lucrative year on record for cybercriminals. The latest numbers show that there were more than 2 billion records leaked in 2016.
Here are just a few of the biggest cyberattacks in 2016:
Government
Even the U.S. government is not immune to cyberattacks. In February, the Department of Justice was attacked by hackers who published contact information of 20,000 FBI employees. That was just a day after the same hackers posted contact information of 10,000 Department of Homeland Security employees. Shortly after these attacks, the cybercriminals taunted the Feds, stating that they did what they said they would do.
High tech
Data from at least 500 million user accounts was stolen from Yahoo! users. The cybersecurity breach actually occurred in 2014 but was only confirmed by Yahoo! this past September. According to Yahoo!, “The account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (the vast majority with bcrypt) and, in some cases, encrypted or unencrypted security questions and answers.”
Healthcare
Hospitals operated by the $5 billion healthcare provider MedStar Health were attacked by ransomware in March. Thousands of patient records could not be updated and in some cases could not even be accessed by healthcare staff. As a result, patients were turned away or were treated without important computer records.
Education
A data breach at the University of California, Berkeley, affected the institution earlier in the year, compromising the financial data of 80,000 students, alumni, employees and former employees. The hackers exposed Social Security and bank account numbers. The breach occurred when software was being patched.
No organization is immune
The attacks just mentioned are just a few of the thousands of cybercrimes that occur worldwide each day. Government, high tech, healthcare, education, etc.—no one is immune from a cyberattack. Cleary, if you’re connected, you’re vulnerable. Fortunately, there are precautions you can take to prevent a cybersecurity disaster. According to the Federal Bureau of Investigation (which is the lead federal agency for investigating cyberattacks), you can protect yourself and your organization from cyberattacks by:
- Backing up data regularly and verifying the integrity of those backups regularly.
- Securing your backups and ensuring they aren’t connected to the computers and networks they are backing up.
Battle cyber threats with Dell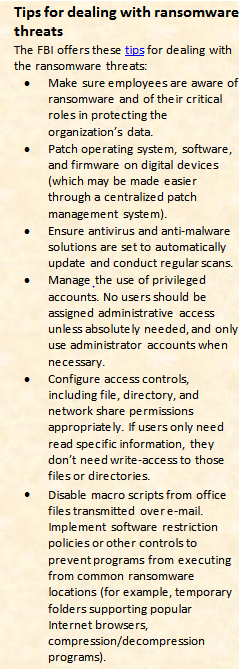
Backing up your data is only part of the data protection equation. The truth is, simple backup is not enough. Not only must backups be scheduled and automatic, you need to be able to verify that they are complete and that the data is recoverable. Here’s how Dell can help:
Isolated Recovery Solutions
Isolated Recovery Solutions (IRS) is a set of solutions that are tailored to meet your specific business needs based on your current infrastructure and desired recovery times. IRS consists of:
- Solutions Planning: Identify applications, recovery times and recovery point objectives.
- Isolation: An isolated data center environment that is disconnected from the network and restricted from users other than those with proper clearance.
- Data Copy and Air Gap: Software to perform data copies to a secondary set of arrays and backup targets as well as procedures to create an air gap between the production environment and the isolated recovery zone.
- Integrity Checking and Alerting: Workflows to stage copied data in the isolated recovery zone and perform integrity checks to verify that data is unaffected by malware.
- Recovery and Remediation: Procedures to perform recovery and remediation should an incident occur.
Mozy by Dell
As acknowledged by the FBI, the most reliable form of protection organizations can leverage to safeguard their data is backup. But simple backup is not enough to ensure that your end users files are protected from ransomware. It’s important to note that common endpoint backup solutions such as a USB drive or network-attached storage device (NAS) are not reliable methods for backing up and safeguarding your data. Ransomware typically spreads throughout an organization’s entire file system, including an attached drive or network share, encrypting both production data and backup data.
When a malware infection is involved, restoration of an endpoint from a backup works best when you can easily select a moment in time from where to restore. Mozy by Dell backs up your important endpoint files to the Dell cloud, so should a cyberattack occur, you can identify the point of infection and the time the malware was introduced to the machine and then restore all of the files for the given user from the point in time just before the malware was introduced. (For an interesting read on cybercriminals, check out Mozy’s Most Prolific Hackers infographic.)
Spanning by Dell
SaaS application users are often surprised to find that their cloud-based data is still vulnerable to data loss and must be managed with the same rigor as data stored on-premises. To protect data from loss due to user error and cyberthreats and maintain compliance with the increasing complexity of audit demands, companies need backup and recovery for their SaaS application data. Spanning by Dell is a backup and recovery solution that provides accurate and granular data recovery from any point in time for G Suite (formerly Google Apps), Salesforce and Microsoft Office 365.
This year and the future
Ransomware is not the only reason that data loss can occur. Other events that pose a threat to your data include natural disaster, user error and hardware failure. In fact, hardware failure is still the number one cause of data loss and/or system downtime, according to the Global Data Protection Index (GDPI). The GDPI also found that on average, the estimated cost to organizations that have experienced data loss is more than US$900,000. Even if 2016 was the year of the cybercriminal, 2017 can be different. Whether the threat to your data comes from hardware failure, cyberattack, natural disaster or user error, Dell can securely protect your business-critical data in 2017 and beyond.