Dell Technologies strives to build trust and a secure, connected world. We work tirelessly to keep your data, network, organization, and customers’ safety top-of-mind – with cyber resilience and security engineered end-to-end into all our products, solutions, and services. From Dell Endpoint Security solutions and VMware Carbon Black Cloud to Dell Trusted Devices, Dell PowerProtect Cyber Recovery, and Cyber Recovery services for multi-cloud, we help you create and maintain a secure and resilient organization even as new threats emerge.
Today, Dell Technologies has expanded this rich set of cyber resiliency and security solutions by introducing cybersecurity features in Dell CloudIQ, the AIOps application for Dell IT infrastructure products. CloudIQ cybersecurity assesses if infrastructure is properly hardened (i.e., that security configurations adhere to the IT team’s chosen policy), proactively notifies IT/security specialists of misconfigurations, and recommends actions to keep their data safe.
Making flexible and robust cybersecurity an integral feature to infrastructure monitoring and analytics applications is aimed at organizations seeking to simplify and automate IT processes. Proven to speed time-to-resolution of infrastructure health, performance, and capacity issues by 2X to 10X¹, CloudIQ stands to help IT teams guard the security posture of their IT environments with less effort.
According to Scott Sinclair, Senior Analyst at ESG, “With cyber attacks presenting an ever-increasing threat to modern business operations, ensuring proper cybersecurity hygiene must be everyone’s priority, not just cybersecurity professionals. Maintaining effective levels of security can be a challenge though as IT infrastructure continues to scale and evolve at a rapid pace. Leveraging machine intelligence, Dell CloudIQ cybersecurity provides substantial benefits to help address this common challenge. CloudIQ’s ability to continuously assess the infrastructure’s security configurations and then proactively notify admins when configurations fall out of alignment, offers a valuable additional layer of protection that businesses need.”
Reduce Infrastructure Misconfiguration Risk
Infrastructure misconfiguration opens your organization to cyber intrusion and is considered to be a leading threat to data security. According to the Open Web Application Security Project foundation (OWASP), insecure configurations are the most common among the top ten security risks. Like a lock and key to your home, proper infrastructure configurations are the foundational first line of cybersecurity defense, and they come in many flavors such as role-based access control, default administrative password, data at rest encryption enabled, and NFS security level.
After you have hardened your infrastructure configurations according to industry standards like NIST and vendor- and infrastructure component-specific best practices, you’ve made it much harder to penetrate. Hardening is the required foundation for a defense-in-depth strategy in which you add other layers of security depending on the value of the assets that you intend to protect.
Above this base layer, you add multiple security protection layers to thwart additional attack vectors according to your organization’s security policy. Typical additional layers are VMware NSX for network micro-segmentation, firewalling, and other security features, as well as VMware Carbon Black for next-generation incident detection and protection.
Leverage Human and Machine Intelligence for Cybersecurity Infrastructure Hardening
Relying on system administrators, data center operations teams or security professionals to log into every system to manually to check and re-check configurations is impractical and leaves infrastructure and your data at risk. A better approach is a software solution that combines these specialists’ expertise (i.e., human intelligence) with automation (i.e., machine intelligence) to continuously do the checking in a prescribed manner to avoid human error and assure completeness of the configuration assessment process.
Dell Technologies has also enhanced CloudIQ with cybersecurity machine intelligence. Our engineers understand systems’ conditions that impact infrastructure health (e.g., capacity and performance issues), then program CloudIQ to continuously perform health checks that recognize conditions that impact health and provide systems administrators with recommendations for remediation. Similarly, our security engineering team has programmed CloudIQ to continuously evaluate infrastructure security misconfigurations and provide recommendations for remediation.
With a recent poll showing that CloudIQ saves organizations as much as 20.5 hours per week on average in system administration time1, IT operations and security teams can expect improved infrastructure cybersecurity efficiencies with the new CloudIQ cybersecurity features.
Ensure Continuous Cybersecurity Checking and Awareness
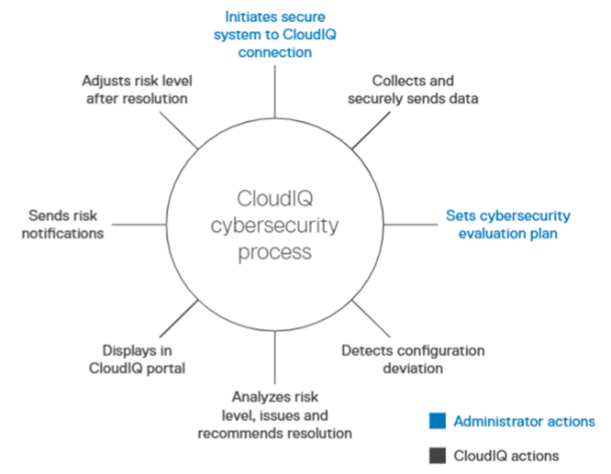
CloudIQ enables a safe and efficient, closed-loop process for comprehensive, 24×7 infrastructure cybersecurity assessment and remediation. You initiate CloudIQ to collect and store your systems’ cybersecurity data via a secure Dell Technologies network; you choose the security configurations to define your policy, and CloudIQ evaluates the data, notifies you of misconfigurations and what to do about them.
CloudIQ initially supports cybersecurity for Dell PowerStore and PowerMax storage systems, and Dell Technologies plans to expand CloudIQ Cybersecurity coverage across its infrastructure systems portfolio.
CloudIQ is another example of a Dell Technologies innovative solution aimed at providing the highest levels of protection, integrity and confidentiality for your most valuable data and critical business systems, so you can get on with your mission.
To read more about CloudIQ cybersecurity capabilities, visit the CloudIQ page.
1 Based on a Dell Technologies survey of CloudIQ users conducted May through June 2021. Actual results may vary.