Graham Porter, EMEA Director of Surveillance and Security at Dell shares some insights on the role of analytics in the defense sector.
Graham Porter, EMEA Director of Surveillance and Security at Dell shares some insights on the role of analytics in the defense sector.
1. If you were a soldier in the field, what sort of analytics are most important to you?
In the field, accuracy matters but speed matters most. Get to the action first with the most was the by-word of Schwarzkopf’s ‘shock-&-awe’. It has been that way since studies of the American Civil War. Military operatives used to rely on ‘line of sight’; historically, battle field data has come through a journey of Balloons, Spotter-planes and Satellites….but the new battle field is a data-rich environment, seeing in many spectrum and analyzing the data in real time from fast storage, analytics and predictive applications.
“One of our biggest fears is that something happens today, and when we do the autopsy we find that two weeks ago we had it, but we did not know because it was buried in something else that wasn’t getting processed.”
Krongard, Exec Director CIA 2001-2004
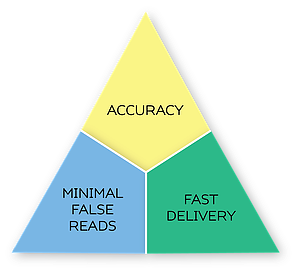
The modern trend is to deliver analytics not simply from cameras, but from multi-waveband sensor analysis (capable to ID concealed weapons on persons of interest, otherwise appearing to be unarmed in naked sight). So the most important analytic feature is accuracy with minimal false reads, but FAST in delivery.
- How is the IT industry delivering this technology? What progress has been made?
Processing speeds are the key to both problems. On-card processors once powerful enough to drive Kray Computing environments would now-a-days be discarded in favour of something from nVidia for instance, capable of out-performing the most expensive multi-threading processors of even 3 years ago. The industry has realized that focusing resources onto a task (searching unstructured data) is best achieved by providing a hardware-backed search application rather than using a multi-purpose processor from the world of consumer IT or telephony.
“Technology has outgrown the industry”
In addition, the IT world has made virtualization a virtue. Small, light and tough equipment running Cloud-based applications have removed the need for in-Hummer mini-racks and two-man carry in-field equipment that was formerly made of ‘regular IT equipment sprayed green’ but is now ‘break-me-if-you-can’ tough and resistant to sand, snow and high humidity environments. The industry has stepped up and made the equipment that can preserve the lives of the equipment-users.
- How do you ensure that your IT is resilient when deployed?
Great question – and we don’t use spears anymore. Meaning, that the weaponry of the next model army is Cyber. If you train a generation of new military operatives to rely on applications to deliver their skill-set, you had better make sure they have the confidence of knowing they have equipment that is impenetrable.
“The weaponry of the next model army is Cyber”
Penetration is an industry in its own right now – testing and probing the other side’s ability to maintain its IT platform is a constant challenge wherein threats come from both friendly and unfriendly actors.
“Tech is virtual, self-defending and self-healing”
- What is the future potential of pattern analysis in the defence industry?
We have talked about how the modern military have managed and will survive through effective execution of data search criteria and speed in assessing threats accurately enough to preserve its shape under pressure and in conflict environments. The technology will get smaller, quicker and more hard to detect. Hot batteries and processor heat-sinks make concealment difficult when the enemy has heat-sensing eyes-on, for instance. Search speeds are being compressed mathematically by pattern analysis, allowing management by exception to aid decision making, improve option accuracy to make conflict survival likely rather than possible. Cannot talk percentages because of sensitivity around the technology, but suffice it to say that technology which appears common today was classified and restricted in recent times and the shake down of technology has allowed wider use of ‘military’ capability in the same way that advances in Formula-1 car braking systems heat energy recycling has led to the implementation of KERS in electric energy-efficient road vehicles now being sold for civilian use.
“Technology which appears common today was classified and restricted in recent times and the shake down of technology has allowed wider use of ‘military’ capability”
Added to that, the ability of a C4 environment to communicate bi-laterally to assets on the ground has meant that for the first time in my lifetime I can see redirection being a possibility in a conflict environment, whereas the traditional view was always that the Main Plan never survived the first meaningful engagement with the enemy. The problem always involved the commanders’ inability to redirect, modify and manage field operative actions in the face of a changing hostile environment. In previous times, a bugle was the way to give commands once the engagement had started, and infantry learned what the calls meant, but not anymore. Data messaging is the new bugle.
“Manage by exception’ – pattern analysis”
This adds up to an environment where the ‘soldier’ has greater value in a modern western army.
We don’t have cannon fodder anymore, we have IT-savvy college grads with fix-it in the field technology capable of giving blood transfusions under fire, and they have so much to live for when the fighting stops.
“Tommy Atkins can now have a Masters in IT, a business degree or has an understanding of the psychology of the military arts. Technology will protect our military while our military will protect us. ‘It’s Tommy this, and Tommy that, give Tommy the boot….but it’s good morning Mr Atkins when the guns begin to shoot…..’ ”
Kipling
- Your personal background in the industry
Principally, I am an electrical engineer and camera engineer who was trained into electronic security and integrated systems and worked into military specialty owing to time with the Royal Navy and managing the electronic security and systems for HM Trident Submarine fleet in (RNA Clyde) Faslane and Coulport Atomic Armaments depots in Scotland, UK.
It really was a testing environment of ‘real’ security and an environment where failure of a security system was unthinkable – the minimum consequence of an off-line system would be groups of armed personnel running continuously around a hazardous perimeter and bringing with them the risk of un-intended escalations from any false alarm, false activation of a perimeter alarm and this was a continuous all-hours full-on security environment with all the stresses and pressures that these special security deployments bring with them. The UK Govt provides special advisory assistance to friends abroad and our people are respected for competence and discrete effectiveness the world over.
- Dell and defense – an overview
The technology delivered by Dell primarily relates to data storage, search tools for unstructured data in single namespace directories and analytics to accelerate access to mission critical data. The largest system we have executed (for a Middle Eastern sovereign state) has been 142Pb of raw storage covering a military port, naval storage and bonded area data providing a secure information in a secure physical and IT environment.
Our Dell accreditation labs run a 5,000-camera system and pass video on test-to-break cycles routinely testing for transmission, accuracy, latency, video-jitter, frame-loss and speed between small hops of data, (equivalent of LA to SF), medium hops, (equivalent of NY to London), and long hops, (equivalent to LA to Singapore). In all cases, our intention is to validate IT architectures and test applications under pressure to deliver highly forensic search and data accuracy over large stores of mixed data types of heterogeneous data. Mixed unstructured data types are common-place and to be expected in an environment which is storing information from applications running on, for instance, SMB files for Windows applications, NFS for file data, HDFS for analytic tools and all data needs to be equally searchable with their meta-data connecting live video, audio and sensor-triggers real time for fast search and viewing with near real time processing on command and control desktops.
The challenge the IT industry in general, and Dell in particular, has risen to is to provide this compute, store and retrieve capability into the hands of combat and C4 (Command, Control, Compute Communicate) working environment not only with resilient software environments but also with hardware which will operate in environments which would have killed IT equipment even a few years ago.
The modern defense operative, in whichever service they operate, now has access to file management technology and search tools and appropriately tough hardware to make the IT-aspects of their roles less prone to failure than at any time in the history our technology.
Graham Porter, EMEA Director of Surveillance and Security, Dell, will be co-leading the workshop on Day 3 covering:
- Introduction to AI, Machine Learning, and Deep Learning
- Resource Requirements for Deep Learning
- Deep Learning Use-cases from Defense and Security
- Deep Learning and Big Data