Edge computing is driven and defined by a massive proliferation of devices generating, capturing and consuming data outside the traditional data center. Capitalizing on this data is critical for maintaining competitiveness in the data decade but securing an exponentially expanding attack surface presents even greater challenges for IT and security staff.
We have seen attacks at the edge increase over the last few years in locations such as retail stores, gas stations and utilities. These attacks are often either cyberattacks that originate from a distance, or physical “man in the middle” attacks in which a physical device intercepts data from legitimate devices, such as gas pumps or registers. This shows not only the increasing need for intrinsic security at the edge, but also the new ways we will need to prepare for and defend against vulnerabilities.
Detecting a cyberattack in the data center can be like finding a needle in a haystack. And a compute environment that spans multiple near and far edge locations and many thousands of devices creates a lot of haystacks to hide needles in. Using a layered approach to protect infrastructure and data at the edge can lower risks and enable you to deploy edge use cases with more confidence.
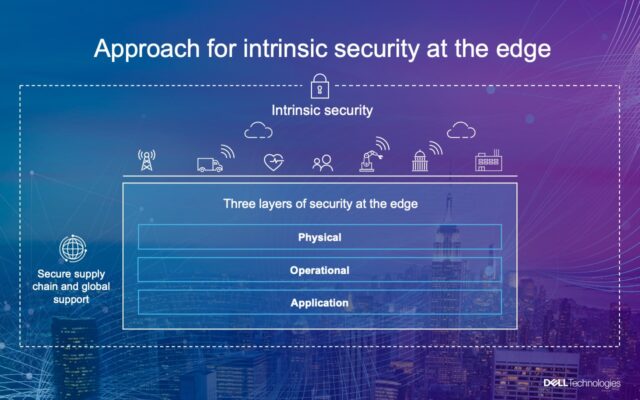
It’s important to remember when creating a strategy for protecting data at the edge that security considerations typically fall into three categories: the physical layer, the operational layer and the application layer.
 Physical layer
Physical layer
Data centers are built for physical security, with a set of policies and protocols designed to prevent unauthorized access and avoid physical damage to, or loss of, IT infrastructure and data stored on these systems. At the edge, servers and other IT infrastructure are likely to be housed in a utility cabinet, under a desk or at a remote location with no regular IT staff on-site. That makes securing physical equipment even more critical at the edge.
Points that you need to consider for physical security at the edge include:
-
- Controlling infrastructure and devices throughout the end-to-end lifecycle, from the supply chain and factory to operation to disposition.
- Preventing systems from being altered or accessed without permission.
- Protecting vulnerable access points, such as open ports, from bad actors.
- Preventing data loss if a device or system is stolen or tampered with.
Operational layer
Beyond physical security, IT infrastructure is subject to another set of vulnerabilities once it is in operation at the edge. In the data center, infrastructure is deployed and operated under a set of tightly controlled circumstances, and data is protected behind the corporate firewall. However, edge environments tend to lack dedicated IT staff, and servers and devices are often deployed by nontechnical personnel. The vast number of devices being deployed, and lack of visibility to these devices, makes securing IT in operation more challenging than in a centralized environment.
Points to consider for securing IT in operation at the edge include:
-
- Ensuring a secure boot spin up for infrastructure with an uncompromised image.
- Controlling access to the system, such as locking down ports to avoid physical access.
- Installing applications into a known secure environment.
Application layer
Once you get to the application layer, data protection looks a lot like traditional data center security. However, the high amount of data transfer combined with the large number of endpoints inherent in edge computing open up points of attack as data travels between the far and near edge to the cloud and main data center and back.
Considerations for application security at the edge include:
-
- Securing external connection points.
- Identifying and locking down exposures related to backup and replication.
- Allowing application traffic from known resources only.
Bring intrinsic security to the edge
When it comes to security at the edge, compromise is unthinkable, and cybercriminals are everywhere. Edge deployments require special focus to provide the same level of robust security as the traditional data center. Dell Technologies takes a holistic approach that builds in security with automation to streamline operations across your core to cloud to edge environments.
Learn more
To learn more about how Dell Technologies can help you implement a comprehensive edge security strategy, visit our edge page.


