One the many advantages of migrating from traditional desktop computers – where data, applications and OS reside on the endpoint – to a Virtual Desktop Infrastructure (VDI) and thin client devices is an increased level of security. With no data or applications residing on the endpoint and a clean session on every reboot, thin clients indeed are very secure.
Even so, the malware threat has become increasingly prevalent and sophisticated, warranting additional measures. In fact, today an estimated 95 percent of security breaches originate at the endpoint and somewhere five new malicious programs are created every second.
About 40 percent of commercially-available thin clients run the Microsoft Windows Embedded Standard (WES) operating system. Using WES, these endpoints can offer the increased flexibility to use a local browser, to install drivers for external peripherals, and run small applications locally. As such, WES-based thin clients must be security-patched regularly (like any other endpoint running a Windows OS), as they still run the risk to be potentially infected by a malicious website, an infected web link, or an infected file residing on a USB stick or other attached peripheral device. No data will be affected on the endpoint itself but there is still a risk of proliferation on the network if the end user forwards a malicious attachment (almost always unknowingly) to a colleague using a traditional PC. For this reason, while desktop virtualization offers a higher degree of network and data protection, it is important to also protect thin clients.
Thin client protection
Microsoft releases security patches for WES each month. Dell packages these security patches so that they can be easily deployed through Wyse Device Manager (WDM) to Wyse thin clients. Dell strongly recommends that all security patches be installed as soon as they become available so that all thin clients are consistent and “up-to-date” with these patches.
Dell also strongly recommends enabling the built-in Windows Defender and Windows Firewall settings before the thin clients are deployed.
The flash memory which stores the operating system images within thin clients is protected from accidental “writes” using a Write Filter (WF). The WF ensures that a thin client can be restored to a known and desired state whenever the device is rebooted. The WF also has an exclusion feature which allows certain files and folders to be “writable” to store user profiles settings. However, incorrect use of the WF exclusion feature can expose files and folders in flash memory to virus attacks. Adding WF exclusions must be carefully considered before the thin clients are connected to the network. If having WF exclusions is required for a particular user environment, we recommend installing anti-virus software to protect the flash from virus attacks.
Watch a 3’ video explaining how Threat Defense works.
Issues with traditional AV/AM solutions
In addition to the above, a best practice includes installing an anti-virus/antimalware (AV/AM) solution on each WES-based thin client. In some organizations, regulations require an AV/AM solution on all endpoints, including thin clients.
The challenge of running traditional, signature-based AV solutions on a thin client is that it can significantly impact the end user, as virus scans are CPU and RAM intensive, and can slow the system to a crawl.
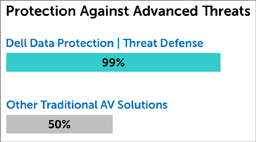
Traditional AV solutions also need daily updates. To make such an update, the Write Filter must be temporarily deactivated. This is a cumbersome daily task and it opens doors to threats in an otherwise highly secure platform. Moreover, such traditional AV can only stop about 50 percent of cyber-attacks and have difficulty preventing “zero-day” attacks.1
For these reasons, only a small percentage of customers have actually deployed a traditional AV/AM solution on their thin clients.
A revolutionary AV solution stopping 99 percent of threats
To proactively protect Windows Embedded thin clients against cyber threats, Dell proposes Dell Threat Defense, an advanced threat prevention solution. This preventive and proactive approach identifies malicious files before they launch, preventing 99 percent of advanced threats by blocking executable malware and ransomware before they execute.1 It uses dynamic artificial intelligence and mathematical models and algorithms derived from machine learning, and is able to prevent zero-day attacks.
An agent runs locally on the thin client, but because it uses only 1-3 percent CPU and has only a ~40MB memory footprint, it has very little impact on end-user productivity. Additionally, it requires infrequent updates (only every 6-9 months) as it isn’t based on signatures created by humans and requiring frequent updates to keep up with the ever growing threats. The technology is also flexible in that it does not require a constant internet connection to offer continuous protection.
Threat Defense satisfies Microsoft requirements for an anti-virus replacement eliminating the need for a traditional AV solution. It also satisfies PCI DSS and HIPAA HITECH compliance.
The solution comes with an optional cloud-based management console, allowing IT to maintain policy, compliance and reporting requirements.
Threat Defense can also be used in mixed environments to protect traditional physical PCs (Dell or non-Dell), Mac OS systems, as well as Microsoft Windows Server systems in the datacenter.
For more information, visit www.dell.com/wyse/shield or contact us.
1 Based on Dell internal testing, June 2016.