How Relevant is Active Directory?
Reliable ole’ Active Directory. A cornerstone of today’s IT infrastructure and still relevant and useful into the future. Or is it? I spoke with some experts from Dell Technologies to find out.
The fundamentals of Active Directory have remained relatively unchanged since the advent of Windows Server 2000 and Windows Server 2003 (aside from incremental improvements over time). The fundamental notion of organizational units, domains, forests, trusts, security boundaries, group policies, LDAP interface, and other X500 standards allowed rich functionality for IT and quickly made Active Directory a standard in the enterprise.
Flash forward to 2020 – the landscape is dramatically different than when Active Directory first came onto the scene. On-premises, public, and private cloud services consumption have multiplied many times over; we live in a multi-cloud world now; collaboration with customers, partners, and guests is now the norm; and, all of this has correspondingly increased the need for new standards in securing resources and services.
I Wanted to Focus on:
1) where are we headed,
2) the relevance of third-party tools, and
3) the importance of Azure Active Directory
I sat down (virtually of course!) with colleagues who work with Dell Technologies customers every day on modernizing their Active Directory. To follow, I’ll share a recap of the key takeaways.
First, Introducing Our Panelists:

Follow Along with our Teams Virtual Conversation
Why Should Active Directory Be Updated and Modernized?
While each of my colleagues commonly help address identity management around compelling events – such as mergers, acquisitions and divestitures, or internal restructuring of an organization – I wanted to understand their thoughts on additional reasons organizations should look at modernizing their identity estate.
Dennis stressed that like any other asset, from a security and patching perspective, it is critical to keep AD current. There are optimizations in each new release of Active Directory that should be looked at and there is also the logical extension into the hybrid mode use cases where customers can take advantage of cloud-based services.
Mike took it a step further in pointing out that customers now may not need their legacy complexity such as multiple domains. In the past, many organizations implemented the old design of an empty root domain and then many resource domains to ease the administrative burden with the technology. Today, there is an opportunity to greatly simplify, reduce both administrative burden and attack surfaces. And he stressed that “modernize” means to look more at cloud-based and SaaS-based capabilities; and it’s clear that the shift in workloads will dictate the need to modernize. As organizations consume more services from the cloud, they will have to pivot to that and that will be a forcing function to modernize.
Chris stressed that new features that come out in succeeding versions of Active Directory should always be looked at, and customers should not stretch things out without risking getting too behind and facing security vulnerabilities from outdated technology.
Why Are Third-Party Tools Needed For Active Directory?
I wanted to get to a discussion about Azure Active Directory. But to do that, I wanted to first discuss third party tools and what are the reasons to employ them (and then see how Azure Active Directory changes that).
On this topic, Dennis brought up the two major solutions in this space, Ping and Okta. Okta and Ping both offer very similar capabilities from a platform perspective although the two solutions have some specific strengths of their own. Ping and Okta both offer Single Sign-On and federation capabilities. Dennis also mentioned that Okta has strong life cycle management features and connects to a wide range of HR systems.
Chris added that the emphasis for using third-party tools is on extending their identity mechanisms. One example he cited was the need to use SaaS based services along with using their existing credentials in a single sign-on experience. Now, traditionally, ADFS is one Microsoft solution for that, but in many cases, ADFS does not have some features customers are looking for, and often times ADFS is complex to implement. Okta and Ping make this easier and also provide additional usability features that make them worthwhile.
We had an interesting discussion around virtual LDAP services. Here, Chris framed the scenario: customers have AD forests that are going to be around for a while, and during organizational restructuring or MAD activity, it can make the transitions for users much easier if the directories that users connect to remain unchanged and some translation is done by tools so that the end-user sees the same directory regardless of what directory is being accessed on the back-end. Solutions such as Oracle’s Virtual Directory or RadiantOne (to cite 2 examples) allow this and also function as LDAP load balancers. This allows users to seamlessly access applications across the board regardless of where the apps sit.
And Mike emphasized two points here: (1) it also avoids the need to migrate applications and masks the need to move applications around (2) It can be thought of as a directory of directory services with business intelligence built-in.
Dave summarized this topic well – customers may have gone to Okta and other 3rd party tools simply because Microsoft’s products in this space have historically been lacking in either capability or ease of use. Now that Microsoft has caught up with AAD, App Proxy, and Seamless SSO, Microsoft has compelling alternatives to these 3rd party solutions. This was a great segue way to my next topic!
What Are the Benefits of Azure Active Directory?
Azure Active Directory has significantly changed the IDP landscape. I wanted to discuss what the panel thought of Azure AD’s role now and in the future.
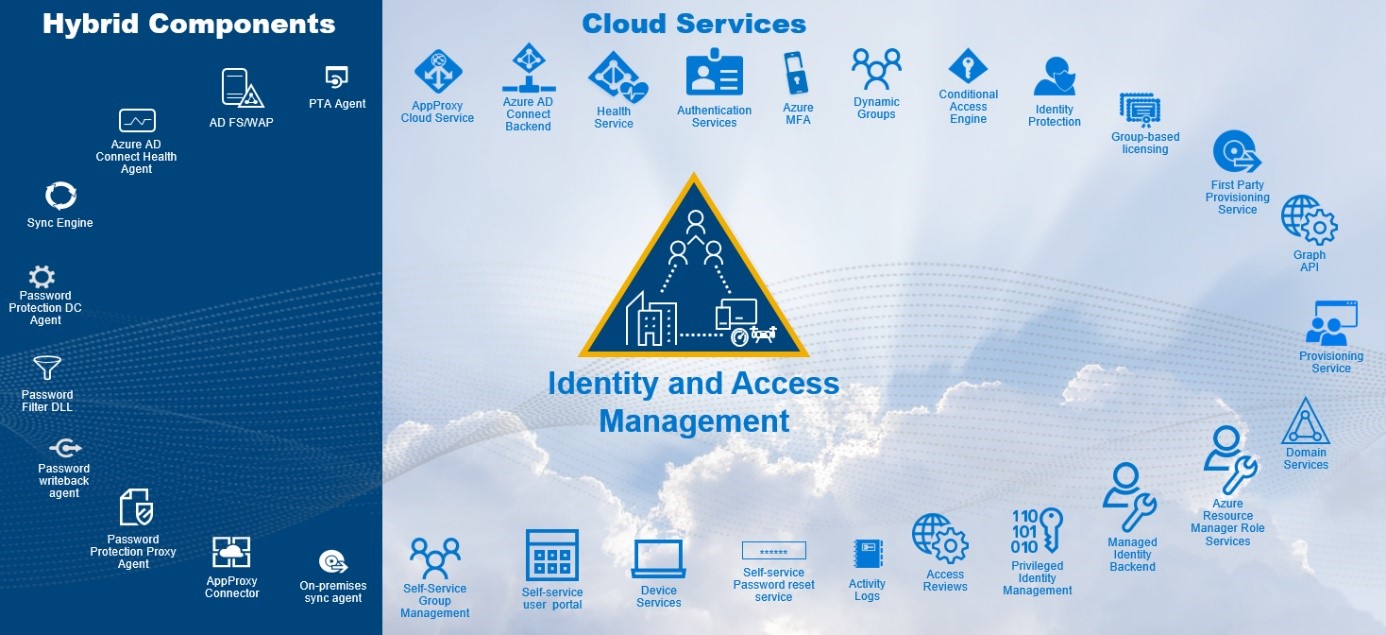
Dennis agreed with my sentiments and commented that Azure AD (AAD) is the future of Microsoft’s directory strategy and provides the pivot point for identities. The IDP capabilities of AAD extend its reach to a far greater extent than on-premise AD, providing rich single sign-on and application integration. Customers should implement Azure AD to take advantage of the rich identity management capabilities like SSO. AAD also has built-in support for end-user self-service functionality ranging from end-user password self-management, group management, and application management.
The figure shows just some of the services that Azure AD can provide.
Chris echoed these views – however – he cautioned that the Azure AD capabilities do not make third-party tools such as Okta and Ping irrelevant. He did agree that 3-4 years ago, the complexity of ADFS and the limited functionality of Azure AD Connect made going to third-parties more compelling. But if customers are looking at broader SaaS services beyond just M365, along with on-premises services, then Azure AD may not get you all the way there.
And Dave added that adopting Azure AD does create some benefits for cloud-first organizations. It allows organizations to shed the “legacy” AD dependencies within an organization. Take System Center Configuration Manager (SCCM) for example, it only works with domain-joined machines. One answer is to transition to Intune so that all management is done from the cloud. While things are moving in this direction (Zero Trust), this journey will take several years to pick up in the market.
Azure AD Domain Services is a new addition to Azure AD capabilities. Chris emphasized important differences between Azure AD and Azure AD DS (managed vs self-managed). On-premises AD and self-managed Azure AD DS (essentially think of it as on-premise AD on virtual machines in the cloud) can do things like extend the schema. Managed Azure AD DS can’t do that. Also, trusts are limited to outbound forest trust only. Replicating some of the on-premises capabilities in the cloud can lead to complexities that need to be understood depending on what you are trying to accomplish.
Overall, Dennis summarized the Azure AD discussion– Microsoft adds features and functionality to AAD at an incredible pace through their “Preview” program in the AAD Marketplace. Microsoft is acting quickly to bridge gaps between AAD and third parties such as Okta, and potentially leapfrogging in other areas. A third party may have an advantage in a particular area today – this will probably not last. For example, ADFS was a sticking point for M365 adoption, so Microsoft added other integration options such as password write-back, and authentication through AAD Connect. And in many cases, the cost efficiencies are substantial in using native Azure AD capabilities.
A key theme that Dennis, Mike, Dave, and Chris made is that security in the cloud is a lot more critical. MFA, for example, for on-prem is useful for administrators. BUT now extrapolate that out – cloud services and resources are so accessible that everyone really should use MFA. Security implications for cloud are a lot more critical. Typically, for on-premises access, organizations could assume an automatic security perimeter (the network perimeter) – whereas, for cloud services, that perimeter is not there as a part of a layered security framework.
Closing Remarks
I enjoyed a lively conversation with this talented group. Here is my summary of key takeaways:
- Active Directory is here to stay
I heard loud and clear that regardless of the advances in cloud directory services and third-party tools:- Active Directory is a fundamental building block
- Organizations have entrenched processes and capability that make Active Directory an integral part of their identity management into the future
- It will be around for years to come
- Modernization is important
My colleagues reflected on the steady stream of improvements and capabilities introduced by succeeding releases of Microsoft’s Active Directory platform – and the importance of keeping up and taking advantage of this capability … or otherwise risk technological obsolescence and security exposure. Moreover, any use of hybrid configurations or using cloud services will necessitate your on-premises Active Directory to be up to date. - Invest in Azure Active Directory functionality
If you consume Microsoft 365 services, which the majority of us do, you will have to have Azure AD. And there is a host of rich functionality to tap into that may be freely available to you; and, it may be cost-effective to implement. It may even replace some third-party tools you currently use. Look into this, get help to investigate, and ensure this is on your strategic roadmap. - Third-party tools have a place
There is definitely space for third party tools to provide additional functionality. However, I also heard:
-
- Standard use cases are shrinking due to Azure AD functionality improvements
- These tools help organizations consume multiple SaaS and cloud services along with on-premises workloads
- They are focused – and much of the value is around ease of implementation, better single sign-on experiences, and a path for migration/co-existence
Active Directory is all grown up and over 20 years old. It has mature siblings, a large extended family, and many friends. So, expect to see this family at all your reunions in the future! Here’s to another 20!