“I don’t know who you are. I don’t know what you want. If you are looking for ransom, I can tell you I don’t have money. But what I do have is a very particular set of skills, skills I have acquired over a very long career. Skills that make me a nightmare for people like you.”
Fine words from Bryan Mills in Taken. Of course, for Bryan, it’s his daughter who is being ransomed. But, in the 21st Century, it’s increasingly data that’s being taken captive, with hackers gaining access to corporate networks and threatening to delete business-critical information unless their demands for money are met.
According to the EMC Global Data Protection Index 2016, more than a quarter of global businesses have lost data in the last year as a result of an external security breach and the average cost of lost data in that time was $914k. Ransomware is a growing threat, and businesses need to rapidly acquire the ‘very particular set of skills’ they need to protect themselves.
The hackers casebook
Taken, of course, was famously a EuropaCorp production, but its rivals at Sony are, perhaps, more familiar with the impact of data breaches. The notorious hacking of Sony in 2014 returned the media company to the working practices of the 80s, forcing employees to communicate through faxes and post-it notes. The 7,000 employees who were paid with paper checks weren’t too thrilled either.
But it could have been worse…
 Code Spaces, a cloud hosting provider and development platform, faced a devastating security breach that happened over a span of 12 hours in an attempt by hackers to extort money from it. The company was ultimately forced to shut down operations indefinitely after the hacker deleted customer data, including most of the company’s backups. Paying the ransom, huge as it might have been, would have probably had less impact on the company – but is that a viable strategy for businesses?
Code Spaces, a cloud hosting provider and development platform, faced a devastating security breach that happened over a span of 12 hours in an attempt by hackers to extort money from it. The company was ultimately forced to shut down operations indefinitely after the hacker deleted customer data, including most of the company’s backups. Paying the ransom, huge as it might have been, would have probably had less impact on the company – but is that a viable strategy for businesses?
Some valuable data
According to the Verizon Data Breach Investigation Reports from 2015 and 2016 we know that:
6 minutes is all it takes for attackers to compromise an organization, 60% of the time
Less than 25% of breaches are discovered in a matter of days
$1,258,670 is the average cost of 1M breached records
Of the 174 million stolen records it tracked in 2011, Hacktivists groups took 100 million.
A very particular set of skills
So what is ‘the very particular set of skills’ that businesses need to protect themselves? The key to surviving a ransomware attack is to ensure that there is a copy of your data that remains beyond the reach of attackers. But that’s easier said than done. Protection data, even if offsite, is, by necessity, network connected. So, even with best practices for backup in place, when businesses come to restore their data, they’ll find that hackers have destroyed that too. What businesses really need, is a virtual panic room for their business-critical data where a copy can be secured and made inaccessible from the network.
Isolated Recovery Solutions
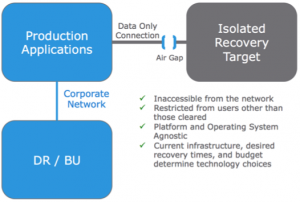 Isolated Recovery Solutions, like the ones offered by EMC, lock hackers out from the most critical data sets by putting an ‘air gap’ between the storage that holds the protection copy and the rest of the network. They also ensure a rapid path to business recovery when needed. Good Isolated Recovery Solutions should feature four key elements:
Isolated Recovery Solutions, like the ones offered by EMC, lock hackers out from the most critical data sets by putting an ‘air gap’ between the storage that holds the protection copy and the rest of the network. They also ensure a rapid path to business recovery when needed. Good Isolated Recovery Solutions should feature four key elements:
Planning and Design – companies need to determine which business-critical systems to protect and how to protect them.
Isolation – an isolated and protected environment within the customer data center is recommended. Measures such as locking down systems and ‘air gapping’ limit exposure to authorized individuals.
Validation – trusted copies can be created at the isolated target site to provide restore points for business-critical systems. Validation tools and methods are applied to ensure the incoming copies have not been compromised.
Recovery and Remediation – restore / recovery procedures to bring their business-critical systems back on track.
The world of cyber crime is evolving rapidly, and businesses need to respond quickly and resolutely if they don’t want their data to be ‘taken’. Isolated Recovery Solutions give organizations a refuge for their data, enabling them to bounce back quickly in the event that their networks are compromised. To find out how EMC can help deliver Isolated Recovery Solutions, visit our microsite – or, to see more of Liam Neeson’s ‘particular skills’ in action, head over to Netflix.